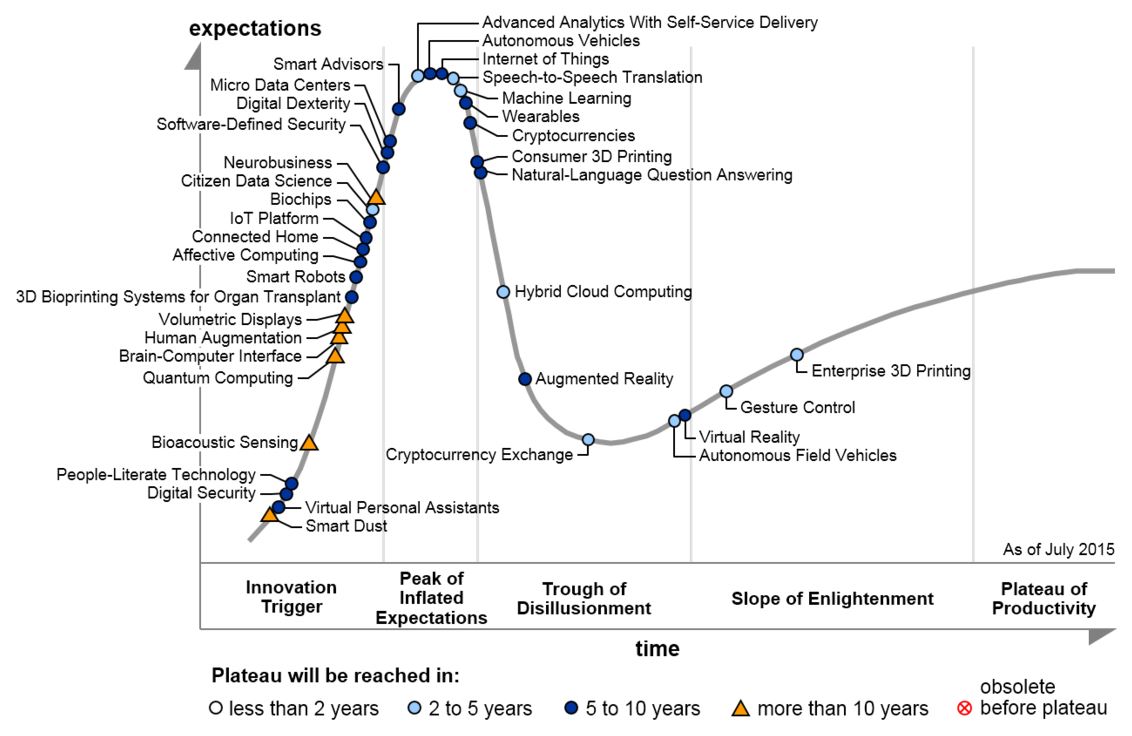
Major changes in the 2015 Hype Cycle for Emerging Technologies (see Figure 1) include the placement of autonomous vehicles, which have shifted from pre-peak to peak of the Hype Cycle. While autonomous vehicles are still embryonic, this movement still represents a significant advancement, with all major automotive companies putting autonomous vehicles on their near-term road maps. […]