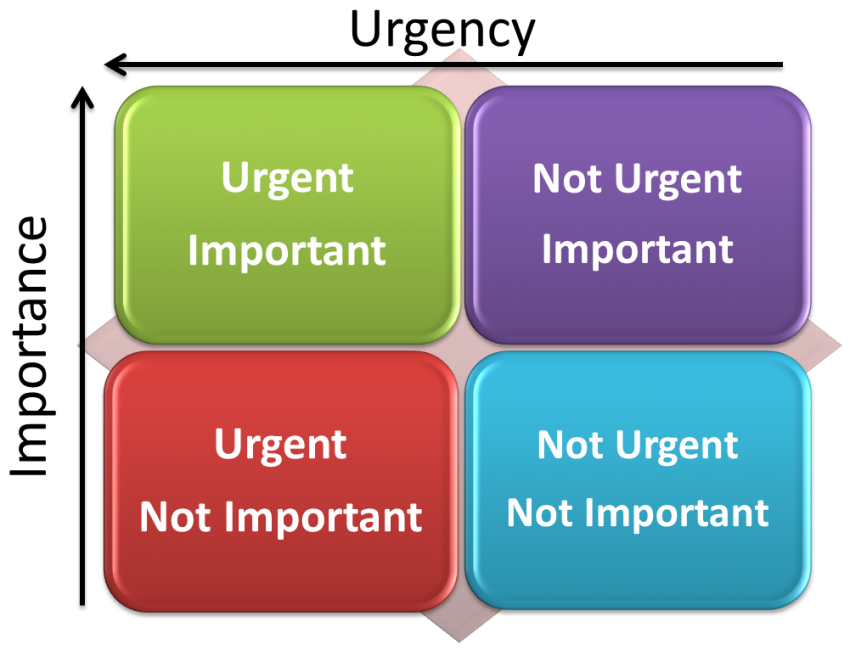
As part of the Software development process we always have to deal with this question: How good is good enough ? Should the team focus on delivering results quickly rather than waiting to build the “perfect” software. To answer this question , I’ve found this successful Kaizen strategy model that has been developed by Japaneses […]