Cisco Operating Systems IOS (Internetwork Operating System) IOS-XE NX-OS Nexus Operating System IOS-XR IOS-XE Features IOS-XE Architecture Application Programming Interfaces (APIs) Programming Languages: Python Ruby Go Support NetConf and Yang Python Telemetry Application Hosting
Fun IOT and Home Automation : Rather than give your smart home device data, and voice commands used to control them, to large tech titans, this talk shows that you can maintain complete privacy using open source software and tools. The open source WebThings Gateway by Mozilla protects users by not sending data nor commands […]
Epoxy Resine is so awesome that I always wanted to give it a try and make something artistic (ish). In this project I carved Cisco Logo and used epoxy resine for central piece and created a natural wood stand for it. I found a piece of wood during one of my weekends hiks near Clear […]
I found wood carving a fun and creative way of spending my spare time I can mix my tools skill and creativity together to make awesome mini characters or other wood projects. My first project was carving the Pikachu mini character for my Son. For this Project I used following tools, you can find most […]
Executive Summary Three billion people – nearly half the world’s population – live on less than US$2.50 a day. Only about 20 percent of households in developing countries have access to the formal financial sector and many of the rest lack access to credit, savings and mortgages (Shah, 2013). This is a consequence of poor […]
As part of the Software development process we always have to deal with this question: How good is good enough ? Should the team focus on delivering results quickly rather than waiting to build the “perfect” software. To answer this question , I’ve found this successful Kaizen strategy model that has been developed by Japaneses […]
During the last Century two major school of economics have been developed, Neoclassical Economics and Keynesiyan Economics. The New Classical school is the modern adaptation of the classical school . It is based on rational expectations it believes Rational agents are always making optimal decisions and firms are always maximizing profits, but the economy is […]
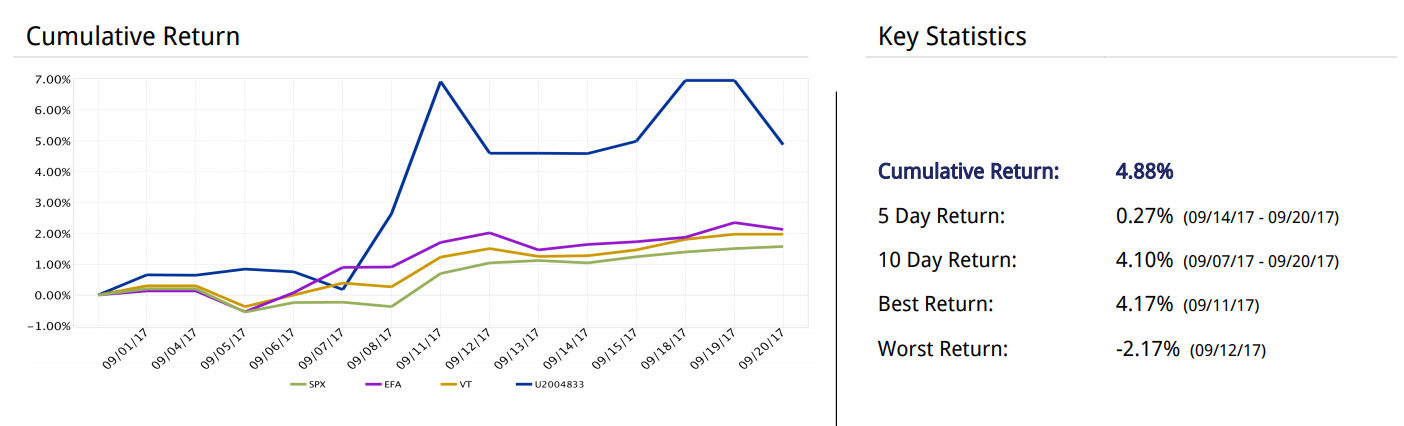
I just started a new stock portfolio for investing in technology sector. here is my portfolio performance for last 20 days comparing to average return from NASDAQ S&P 500 companies. Update: now in December 2017 after 4 month my portfolio performance is about 260% thanks to bitcoin FOMO (“Fear Of Missing Out”) and growing IPO […]
By Saeed Karimabadi, Amanda Bennett, Yang Ji, Yufeng Zhou and D Abstract In this report, we have studied the United Airlines Corporate Social Responsibility Report (CSR). What company has claimed and what it has done. Company Background United Airlines, Inc., commonly known as United, is an American airline headquartered in Chicago, Illinois. United operates a large […]
In this paper, I’m going to compare the transparency of my recent two employers with their employees and how that can affect the ethical relationship in the workplace. For the past three years, I have been working at Lumentum Company, which is a public and international company, producing Fiber optic related communication equipment. Before that […]
Being a software developer and also an Stock trader, it is hard to not get persuated to practice algorithmic trading. Over course of my career I had done multiple data processing algorthms, In 2017 I took a Data mining course as part of my MBA program with concentration in Data Analytics and that course showed […]
By Saeed Karimabadi Executive Summary: Canadian Tire Corporation (CTC), with 495 dealer-owned Canadian Tire stores, 436 FGL Sports banner stores, 297 gasoline outlets, and 383 Mark’s stores, is one of Canada’s largest and most iconic retailers. While CTC’s core business is Retail with Canadian Tire Retail (CTR) as its core platform, the generational shift CTC […]
People who emphasized too strongly the fact that they’re professionals usually are not very good at what they do. What really adds up to professionalism is being very good at what you do in a very modest way. Herb Kelleher, former Southwest Airlines CEO
Introduction: With laws requiring motorists to use hands-free communication devices, an increasing number of vehicles are equipped with Bluetooth™ technology. Copmany is proposing a system comprised of detectors installed along the road or highway. This system detects vehicles that are equipped with Bluetooth™ technology. Vehicles are detected totally anonymously, and data are generated on their average […]
This is a while I’m trying to find historical stock data to build an AI system. Sadly it’s not as easy as it appears. I’m putting together my findings here: Option 1: Using Yahoo’s CSV approach above you can also get historical data! You can reverse engineer the following example: http://ichart.finance.yahoo.com/table.csv?s=AMZN&d=0&e=28&f=2016&g=d&a=3&b=12&c=1996&ignore=.csv Essentially: sn = TICKER a […]
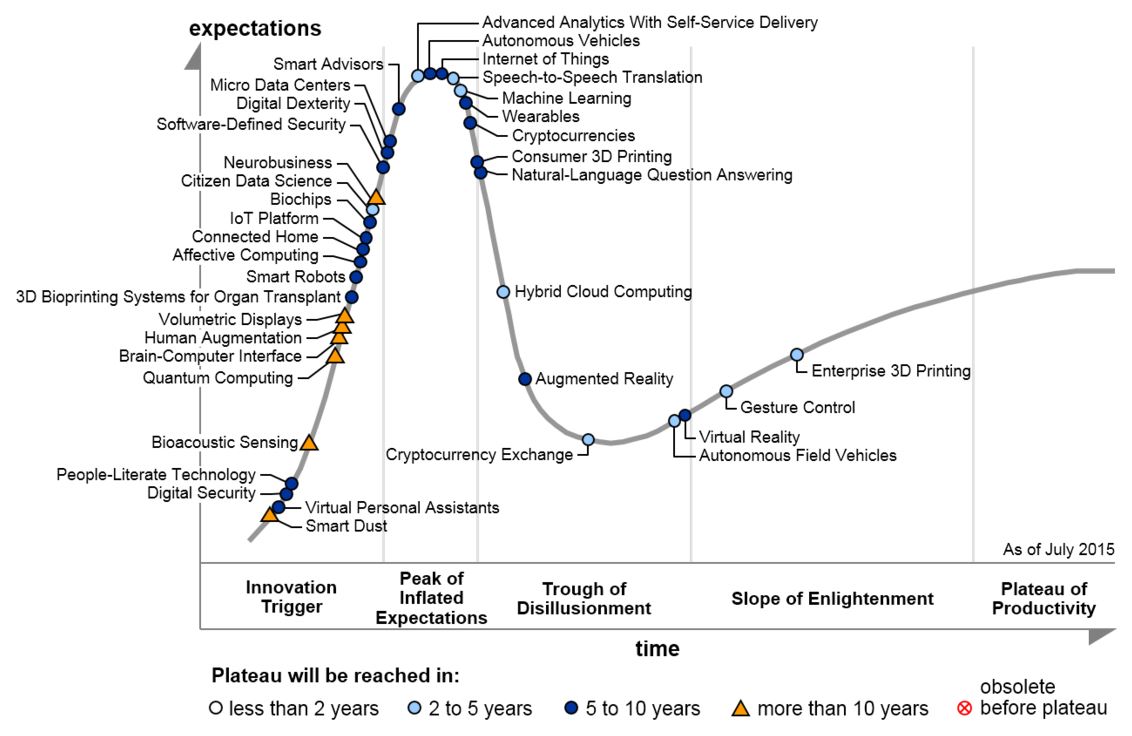
Major changes in the 2015 Hype Cycle for Emerging Technologies (see Figure 1) include the placement of autonomous vehicles, which have shifted from pre-peak to peak of the Hype Cycle. While autonomous vehicles are still embryonic, this movement still represents a significant advancement, with all major automotive companies putting autonomous vehicles on their near-term road maps. […]
Saeed wrote this case analysis as a marketing course practice. The author does not intend to illustrate either effective or ineffective handling of a managerial situation. Introduction Jill’s table is a small business located in London Ontario focused on kitchenware and specialty food. During the years, Jill Wilcox, the owner of the Jill’s Table has […]
Security Analysis: Malicious or criminal attacks are most often the cause of a data breach globally. According to IBM Report on Security Breach cost (IBM and Pnemon Institute, 2015) Forty-seven percent of incidents involve a malicious or criminal attack, 25 percent concern a negligent employee or contractor (human factor), and 29 percent involve system glitches […]
Summary: Each company needs to asses and prioritize different risks involved in IT domains. They need to establish the data safety policy describing the accepted level of security and continuity for each section of their business and different level of data access. Also they have to monitor and re-assess the risks continuously. Analysis: Doing business is always […]